About the Performance Evaluation Program for IT security Products
A program in which the performance evaluation of an IT security product is evaluated according to standards and procedures, and report the result how the product responds to normal and harmful traffic in the operating environment.
The purpose of the program
- 1. To support the technical improvement of Information security businesses and help buyer(=demander) select better products when they purchase IT security products.
- 2. Based on verified performance evaluation, objectivity is secured to shift the focus of the market from price to performance, enhancing the nature of Information security industries.
Related laws and regulations (legal foundation)
- Article 38 (The Announcement of the Standards for Information Protection Systems) THE FRAMEWORK ACT ON NATIONAL INFORMATIZATION
- Article 35 (The Complementation of Information Protection Systems) of the Enforcement Decree of THE FRAMEWORK ACT ON NATIONAL INFORMATIZATION
- Article 52 of the Act on Promotion of Information and Communications Network utilization and information protection, etc. (KISA)
- Article 17 (Supporting Performance Tests,) ACT ON THE PROMOTION OF INFORMATION SECURITY INDUSTRY
- Article 10 (The Method of Performance Evaluation and Designation of Performance Evaluation Agencies,) the Enforcement Decree of ACT ON THE PROMOTION OF INFORMATION SECURITY INDUSTRY
An overview of our Evaluation services
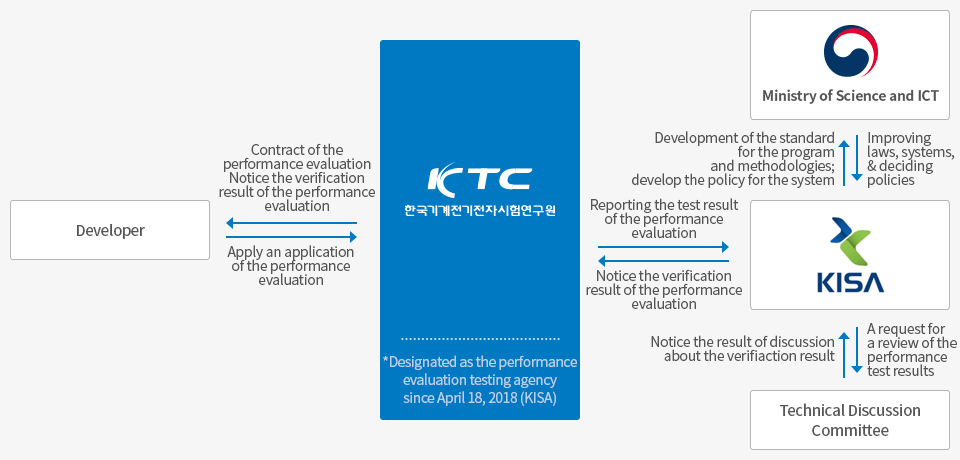
The evaluation and certification processes
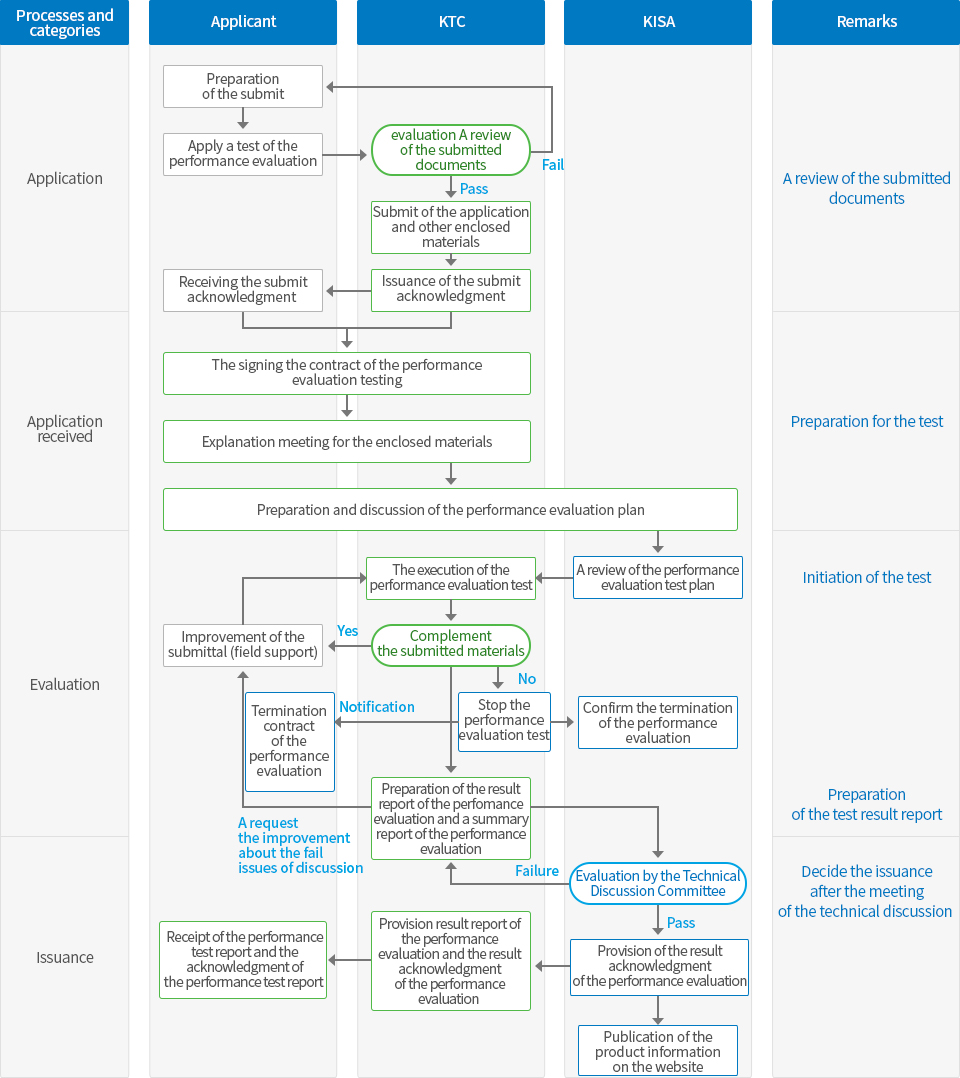
The scope of the performance evaluation
Equipments of the performance evaluation
Inquiry and Contact Information
Visit the website of the responsible department
Click the button below to jump to the main webpage of the responsible department, where you can find the contact information of the officers in charge.